Hi everyone,
Today, we will try to give you a simple explanation of a life-saver feature: SSH tunnels and port-forwarding!
There are many cases in which you will find SSH-tunnels very useful:
- when your remote server is not directly accessible (behind a firewall or in a DMZ)
- when your remote program only binds to 127.0.0.1 (if you are using a mysql instance only bound to localhost on your web server for instance)
- when you want to secure a protocol (like VNC or X11) by transporting it through an encrypted SSH channel
- when you connect to a home computer, NAS or Raspberry Pi from the Internet
- when you need to get through a network equipment where only SSH protocol is allowed
- when you open a connection to a remote server and need to easily open a reverse communication channel from the remote server to your local computer
In all these situations, you will be able to achieve your goal easily thanks to SSH-tunnels.
Simple explanation of SSH tunnels and port-forwarding
If you are not used with SSH tunnels, here is a simple graphical explanation on how a simple SSH-tunnel works:
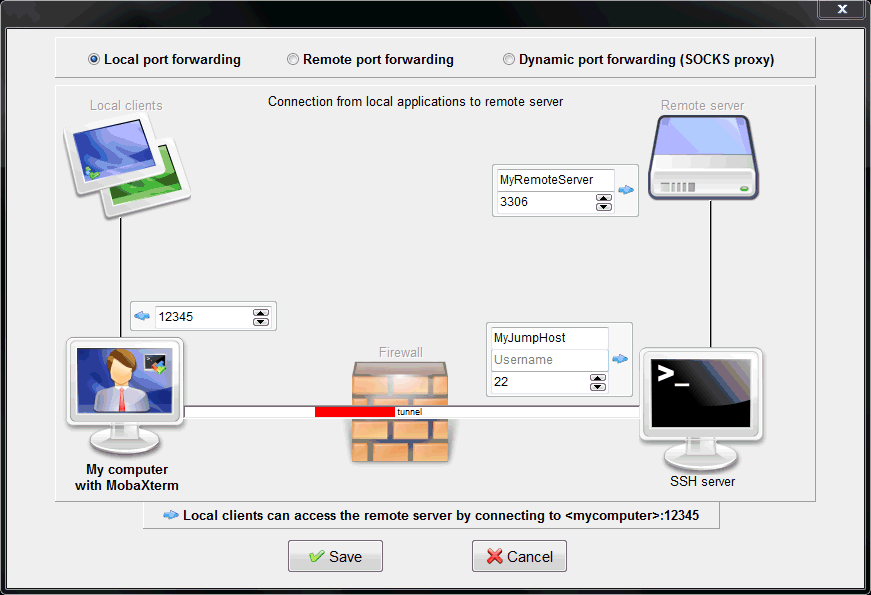
This screenshot explains local port-forwarding mechanism: local clients need to connect to a remote server which cannot be reached directly through network. A SSH connection will be established from “My computer” to “SSH server” (used as a “jump host”) and the local clients will use this tunnel in order to directly connect to the remote server.
In the example above, the remote server is running a MySQL database on port 3306. In order to reach it directly, the client applications will have to connect to “localhost”, on port 12345.
Their connection will be automatically forwarded through the encrypted SSH tunnel, go through the jump host and reach the remote server on port 3306.
This picture shows the mechanism called “Local port forwarding”, but there are 2 other kinds of port-forwarding:
- Remote port-forwarding: this is the same principle, a tunnel is opened from local computer to jump host, but the aim is to connect from remote server to local computer.
- Dynamic port-forwarding: same principle, but the dynamic tunnel allows connection to any remote hosts and any remote ports. Local applications should be compatible with this protocol and allow configuration of a "SOCKS proxy".
How to connect to remote computers using a jump host
MobaXterm makes it really easy to connect through a jump-host.
Let’s say we want to reach ServerC through SSH, telnet, RDP or VNC. Unfortunately, ServerC cannot be reached directly on the network, you have to connect to ServerB first, then from ServerB to ServerC. In MobaXterm, you just have to:
- create a new SSH, telnet, RDP or VNC session
- put "ServerC" in the "remote host" field
- open the "Network settings" section
- check "Connect through SSH gateway (jump host)
- fill-in required information in order to connect to "ServerB"
This will silently create an encrypted SSH tunnel to ServerB and then use this tunnel in order to connect to ServerC.
How to connect to my Cisco router or switch behind a firewall?
It is sometimes hard to work with remote network equipments, especially when they only allow telnet connections and when telnet is disallowed in your company firewall.
There is a simple workaround if you can reach a server behind the firewall using SSH: let’s say the server you can reach using SSH is called “RemoteSshServer”.
- In MobaXterm, just create a new telnet session.
- Put your Cisco equipment address in the "remote host" field. This address should be the one which will be used by "RemoteSshServer".
- Open the "Network settings" section and check "Connect through SSH gateway (jump host)
- Fill-in required information in order to connect to "RemoteSshServer"
This will silently create an encrypted SSH tunnel to RemoteSshServer and then use this tunnel in order to connect to your network router.
How to reach my server behind multiple jump hosts?
Well in this case you will have to manually create your SSH tunnels. Do not worry, this will not be too hard.
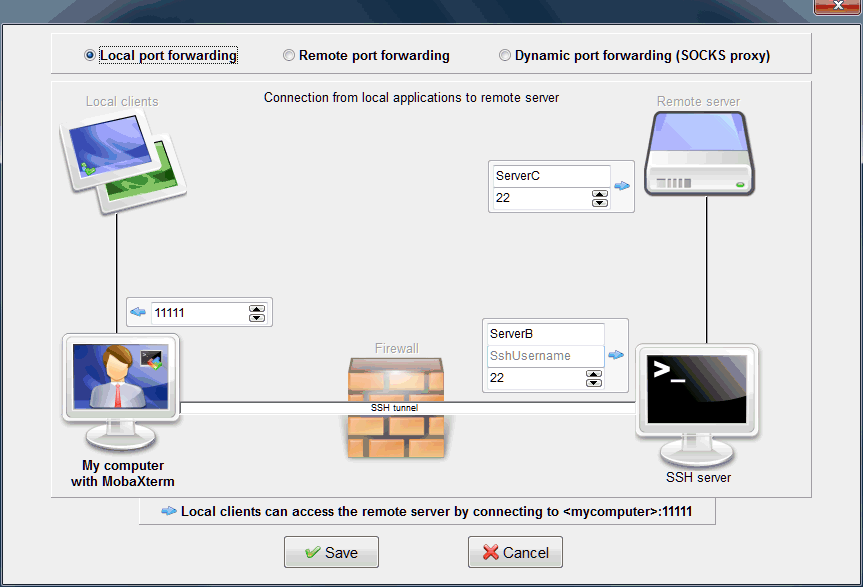
Let’s say we want to reach “ServerD”, by using “ServerB” and “ServerC” as jump hosts.
- Open "MobaSSHTunnel" from MobaXterm "Tools" menu
- Click on "New SSH tunnel" and create a new local SSH tunnel to "ServerC" by using "ServerB" as jump host. Type "11111" in the "Forwarded port" field
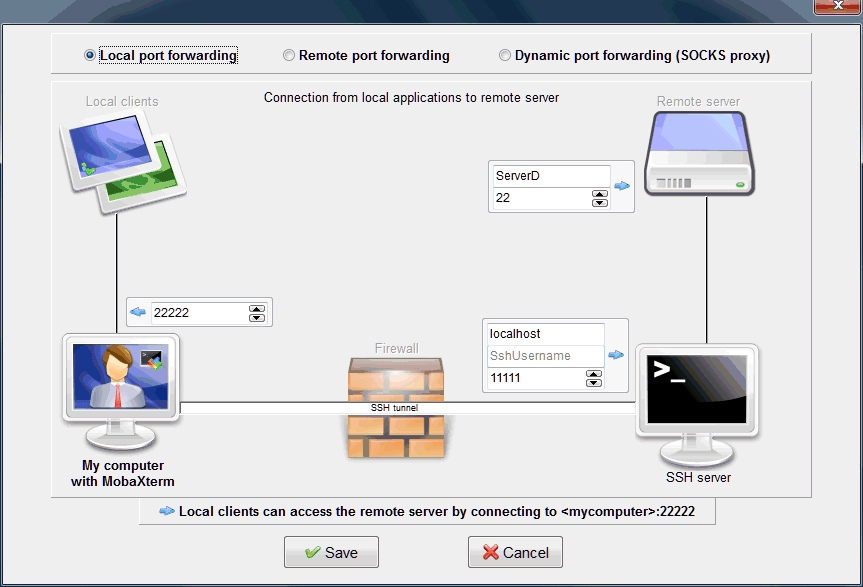
- Click on "New SSH tunnel" again and create a 2nd local SSH tunnel to "ServerD" by using "localhost" port "11111" as jump host. Type "22222" in the "Forwarded port" field
- Verify that the 2 tunnels are properly started
- Create a new MobaXterm session and connect to "localhost" port "22222" in order to directly reach "ServerD"
First SSH tunnel:
Second SSH tunnel:
How to reach my remote SQL server which only binds to localhost?
In this case you will also have to manually create your SSH tunnel.
Let’s say we want to reach a MySQL instance on “MyWebServer”:
- Open "MobaSSHTunnel" from MobaXterm "Tools" menu
- Click on "New SSH tunnel"
- Create a new local SSH tunnel to remote server localhost, using remote port 3306, SSH server MysqlServer (port 22), and forwarded port 3306
- Connect to your remote MySQL database using your favorite client tool by using remote address localhost, port 3306
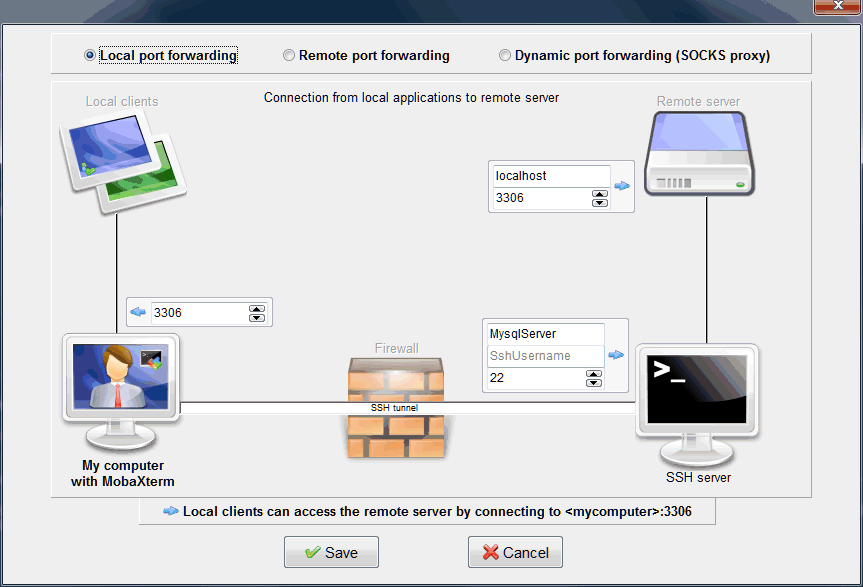
How to securely reach my home computer, Raspberry Pi or NAS server through Internet?
If you have a Raspberry Pi, there is a specific procedure for the Raspberry Pi described in this article.
For any other equipment, here is the basic procedure:
- Go to https://whatismyipaddress.com in order to know your public IP address (the address from which your house can be reached from the internet): let's say that the public IP address you obtained is 36.36.36.36 and the IP address of your equipment on your home network is 192.168.1.10.
- Add a new "Port forwarding" entry in your internet router with the following configuration: port "22" from the internet is forwarded to "192.168.1.10" on port "22". It means that when someone from outside your house connects to your internet router on port 22 (SSH), its connection is redirected to your home equipment on port 22 (SSH).
- From outside your home, launch MobaXterm on a Windows computer connected to the Internet
- Create a new SSH session, fill the "remote host" field using your public IP address 36.36.36.36 and click on "OK"
How to set up a simple SOCKS proxy?
A SOCKS proxy is basically a service which performs “dynamic port forwarding”. In order to set up a simple socks proxy, you just have to
- open "MobaSSHTunnel" from MobaXterm "Tools" menu
- click on "New SSH tunnel"
- check the "Dynamic SSH tunnel" setting
How to secure my VNC connection using SSH?
Basic VNC protocol is not secured, so in order to encrypt data, you can direct VNC traffic through a SSH tunnel. You will need a SSH server installed on the host where VNC server is.
- On your remote server, configure the VNC-server program in order to listen only to localhost (127.0.0.1)
- In MobaXterm, create a new VNC session
- Set the "remote host" field to "localhost"
- Open the "Network settings" section and check "Connect through SSH gateway (jump host)
- Fill-in required information in order to connect to your remote SSH server
This will silently create an encrypted SSH tunnel to your remote server and then direct VNC traffic through this tunnel.
We hope that these explanations about SSH tunnels and port-forwarding will be useful for your daily work.
If you want to read more on the subject, you can read the Wikipedia articles about tunneling or port-forwarding.
